Ksama Arora
IAM Policy Hands On
If you remove a user from a group, the inherited policy permissions will be lost by the user.
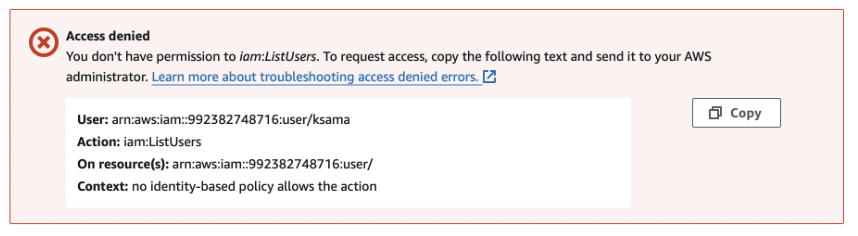
If say through the root user, you attach a policy say IAMReadOnlyAccess to the user, you will only be able to read anything on the IAM. You will be denied of any other access if tried.

Example: you create a user group names developer and attach a policy AlexaForBusiness to it, and a user group admin with policy AdministratorAccess. If you add a user say ksama to both these groups, and also attach a policy say IAMReadOnlyAccess directly to this user, then this user will have 3 permission policies attached.

Looking at some policies in detail:
- AdministratorAccess Policy: All services have full access to this policy. Allows any action () on any resource ().
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": "*", "Resource": "*" } ] } - IAMReadOnlyAccess: IAM is authorised with Full: List Limited: Read. Note: Get* means that anything that starts with Get and has something afterwards is authorized.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "iam:GenerateCredentialReport", "iam:GenerateServiceLastAccessedDetails", "iam:Get*", "iam:List*", "iam:SimulateCustomPolicy", "iam:SimulatePrincipalPolicy" ], "Resource": "*" } ] }
Create Policy using Visual Editor or a JSON Editor